HTTP vs HTTPS Sites
These are the two types of sites, HTTP being insecure and HTTPS being secure.
There are two types of sites, HTTP and HTTPS sites. One is obviously more secure than the other but why and how exactly is it more secure? The following sections will give an overview of this.
Popcorn Hack: Why is HTTPS more secure than HTTP?
HTTPS is more secure as it uses TLS (SSL) to encrypt normal HTTP requests and responses, and to digitally sign those requests and responses
HTTP
In this case, we are looking at posting passwords without encryption. Going to vulnweb.com, a common test site for vulnerabilities, we can test and see how insecure data can be dangerous. Keep in mind that this is illegal to do on actual websites and networks.
We use a network scanner to track information between the internet and the client device. In this example we enter test data into the username and password inputs:
It looks like everything is secure to the user, the password is blocked from your general view and the website seems slightly trustworthy with its formatting. This is, however, very far from the truth, especially when we begin using the network scanner to see the traffic.
Here we see something that we are all familiar with, a POST. When we open the contents of this post, we can see the following:
We can see the password in plain text that was inputted in the password field of the website. This is a very clear reason why you should never store your passwords without the use of encryption, like with TCP and TLS handshakes.
HTTPS
If I, for example, log into MyPlan, we can see an entirely different story:
Here we see no POST, mainly because we are using something called TCP and TLS handshakes, which create an encrypted connection between the user and backend server.
TCP and TLS
Describing the encryption and communication protocols between servers for secure data.
This handshake process allows for a secure and encrypted method for sensitive data to be transferred between the client and server.
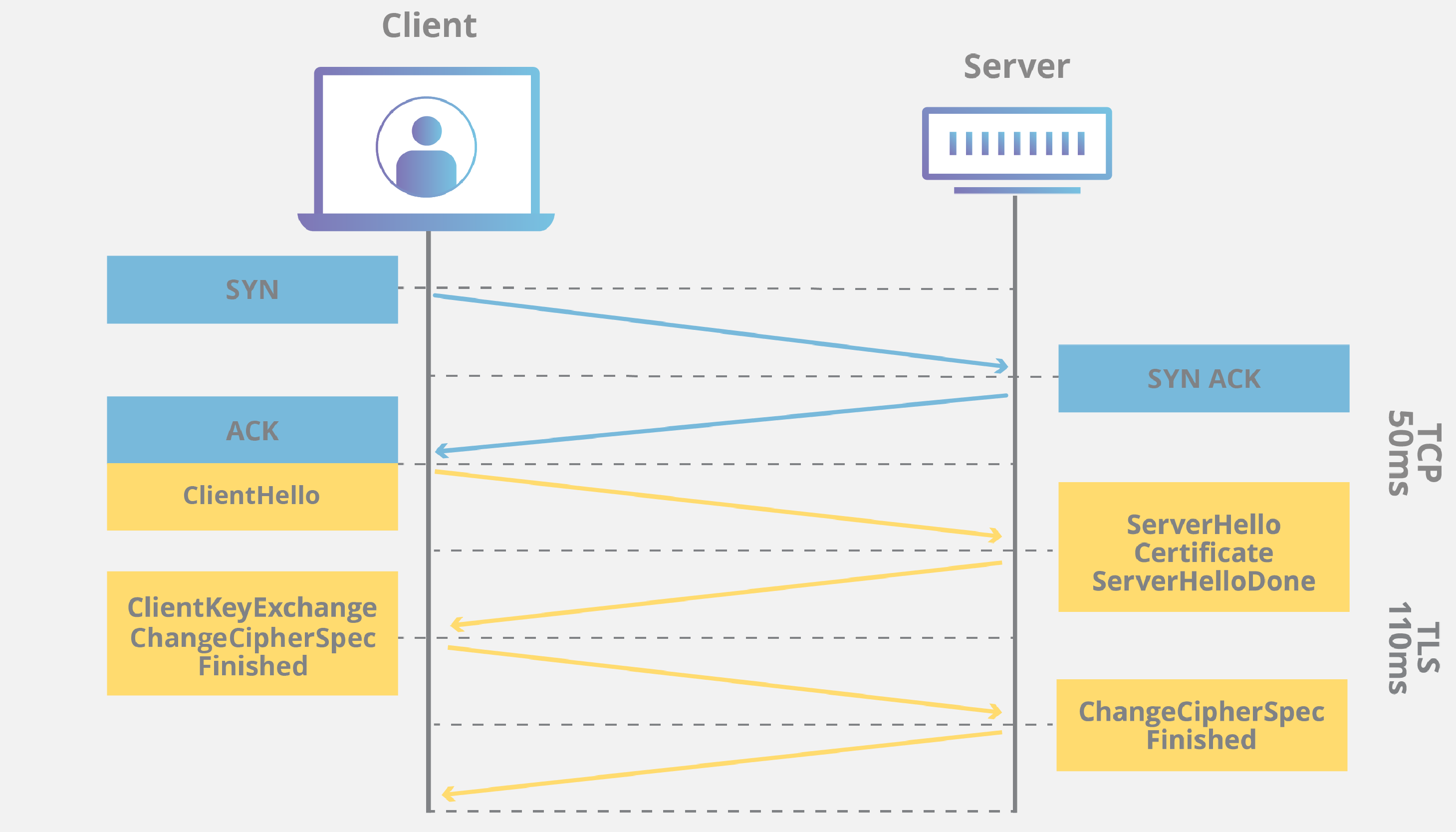
TCP Three-Way Handshake
The step process of connecting to the server securely.
A TCP handshake, more specifically a three-way handshake, is how the client and server initially establish a connection that is later used for communication. This method isn’t secure by itself however it helps later establish a TLS connection which is more secure.
Process
- SYN (Synchronize) - initiates connection
- sends ISN (initial sequence number) that is used as an identifier, organizing the data sent/received correctly
- SYN-ACK (Synchronize-Acknowledgement) - acknowledgement of connection
- sends its own ISN and the client’s ISN, confirming a connection
- ACK (acknowledge) - completing the connection
- indicates that it knows the server’s ISN
The server is now ready for a TLS connection.
TLS Handshake
This is where the encrypted data is transferred between the client and server. This exchange varies on the version of TLS that is used, however they all have a similar series of steps.
This is how secure communication of secure information is sent between the client and server. This is how the more common TLS (Transport Layer Security) typically works, and the process can be seen here for a more in depth look.
Process
- ClientHello: Client sends supported cipher suites, compression methods, and a random number to the server.
- ServerHello: Server responds with its chosen cipher suite, compression method, and its own random number.
- Key Exchange: Server provides its certificate and key information, allowing the client to verify the server’s identity.
- Pre-master Secret: Client creates a pre-master secret and encrypts it with the server’s public key. This encrypted pre-master secret is sent to the server.
- Master Secret: Both the client and server use the exchanged random numbers and the pre-master secret to independently compute the master secret.
- Finished: Both sides confirm that the handshake is complete and they can start encrypted communication using the derived master secret.
HTTPS vs HTTP
Distinguishing the differences between the two for secure browsing and data transfer.
The difference between HTTP and HTTPS lies in the added layer of security, thanks to the SSL/TLS protocols. HTTPS stands for HyperText Transfer Protocol Secure, and it ensures that the data exchanged between a user’s web browser and the website’s server is encrypted and secure.
Here’s a quick comparison:
- HTTP (Unsecured):
- Data is transmitted over plain text.
- No encryption is used, making it susceptible to eavesdropping.
- Vulnerable to man-in-the-middle attacks.
- HTTPS (Secured):
- Data is encrypted before transmission.
- Secured by SSL/TLS protocols.
- Protects against eavesdropping and man-in-the-middle attacks.
In conclusion, while HTTP is faster due to the lack of encryption overhead, HTTPS is crucial for securing sensitive information. It’s especially important when dealing with login credentials, personal data, and financial transactions on the web.
Conclusion
Recap on the importance of secure browsing and data transfer.
In conclusion, understanding the difference between HTTP and HTTPS and the role of TCP and TLS in secure data transfer is crucial in the realm of cybersecurity. Using unsecured connections like HTTP can expose sensitive information to malicious actors, leading to potential data breaches and unauthorized access.
Always prioritize HTTPS when accessing websites, especially those that involve confidential information. The use of encryption protocols like TLS ensures that the communication between clients and servers remains confidential, integral, and secure.
By being aware of these security measures, users can make informed decisions and contribute to creating a safer online environment. Cybersecurity is a shared responsibility, and staying informed about best practices is key to mitigating potential risks and threats.